This challenge gives us a .cap file called BobertsonNet.cap

From this, we can tell that this is a cap of some Wi-Fi traffic.
I did a search for BobertsonNet, and it returned a device broadcasting the SSID: BobertsonNet
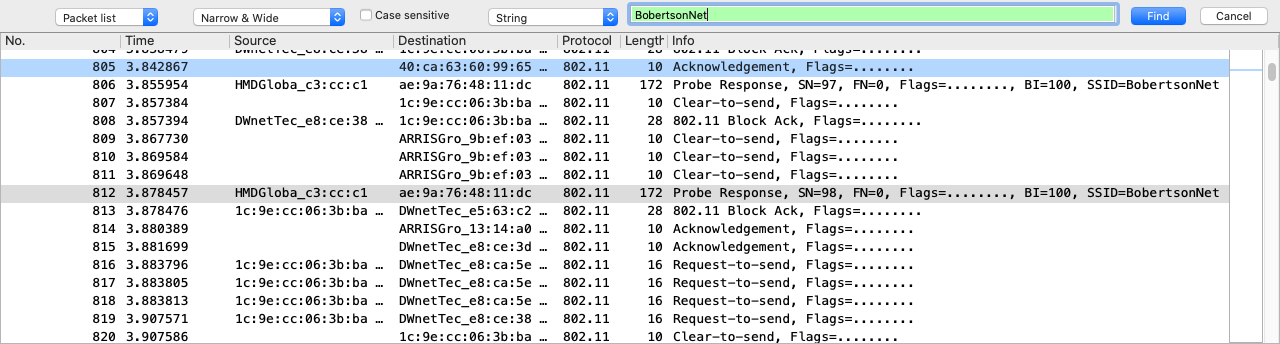
Something I noticed cruicially, is that all of this data is “QoS” data. QoS is quality-of-service data, and in this context, wireshark uses “QoS” data as a broad wrapper for encrypted data. Meaning that we’re probably going to have to break the encryption between some endpoint devices.

And then I came across this packet.

This is an EAP packet. EAP if you don’t know, is an authentication protocol that is used over 802.1X
EAP uses a 4-way handshake to authenticate. So lets look for that handshake between these clients.
Let’s checkout the communications between these devices.
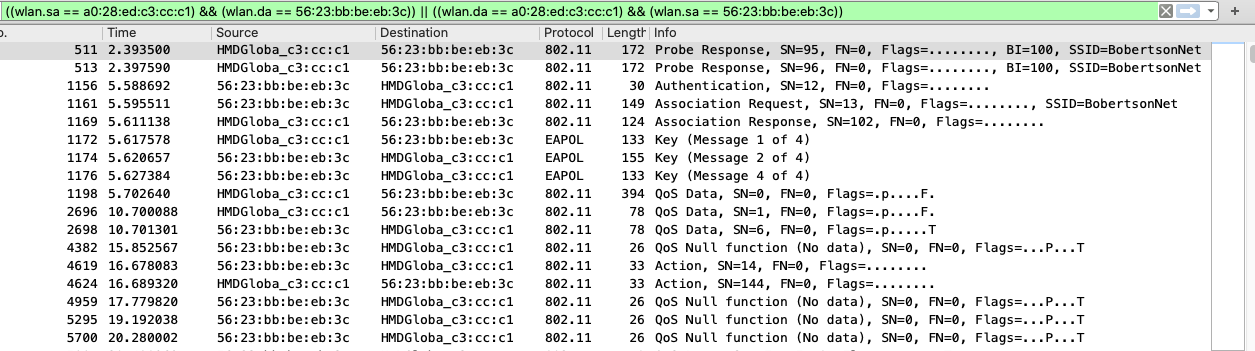
And here we can see what’s going on.
Let’s use this picture as to help explain what is going on.
I would also like to point out, that not all of the transmissions are shown in this capture. In practice this can be for many reasons such as interference.
- We see that the router gives a probe response.
- The “mobile station” sends an authentication request.
- The “mobile station” sends an association request.
- The router/AP sends an association response.
- The EAP handshake starts.
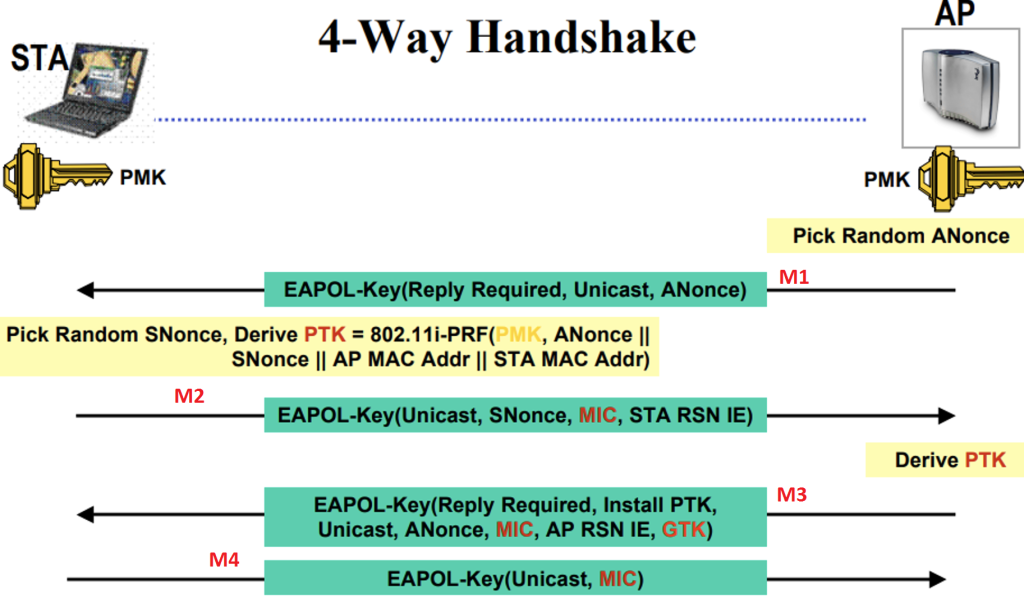
But wait, this is a 4-way handshake, but there are only 3 parts of the message. However will we decrypt the communications here?
Don’t you worry because all hope is not lost.
EAP does not actually transmit the password in the handshake. In actuality, both devices know the password. They both use PBKDF to derive a Pre-Shared Key between one another.
In EAP, the PTK, and MIC are the importent keys that need to be generated in order to authenticate.

In message 1, the access point sends the client a NONCE.
In message 2, MIC verification will be done, and sent back to the access point.

Message 3 is supposed to send back the MIC, as well as the GTK, however we don’t have message 3, but that’s okay. All we need to do is find the PSK to make the MIC verification hashes match.
This explaination is a gross-oversimplification so please check out this blog post for a very detailed explaination
Because we have both message 1, and 2 we can use airdecap to brute force the password, to generate the PSK.
Running it through airdecap-ng, the password we get is “billybob1”.
Let’s use that password to decrypt the conversation.
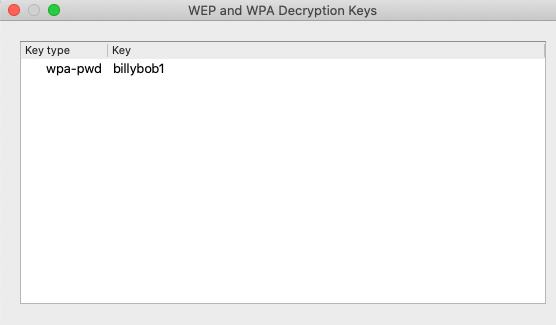
And now we have our decrypted communications!!
Luckily for us, airdecap gives us the decrypted cap.
Grepping through the file for “iris” gives us the flag!!
irisctf{4ircr4ck_g0_brrrrrrrrrrrrrrr}